Workforce Identity Federation is a feature of Google Cloud Identity and Access Management (IAM) that allows you to use an external identity provider (IdP) to authenticate and authorize users to access Google Cloud resources. This means you can manage your users and groups in your existing IdP, such as Microsoft Entra ID, and grant them access to Google Cloud without having to create and manage separate Google accounts for each user.
In this post, I will walk you through the process of configuring Workforce Identity Federation between Google Cloud and Microsoft Entra ID. By the end of this guide, you will be able to sign in to Google Cloud using your Entra ID credentials.
prerequisites
Before we begin, you will need the following:
-
A Google Cloud organization.
-
A user with the Organization Administrator role in your Google Cloud organization.
-
A Microsoft Entra ID tenant.
-
A user with the Global Administrator role in your Entra ID tenant.
-
The
gcloudcommand-line tool installed and configured.
create workforce identity pool
create Microsoft Entra ID application and secret
First, we create a Microsoft Entra ID application using the Microsoft Entra admin portal.
Register a Web application. The redirect URI will be https://auth.cloud.google/signin-callback/locations/global/workforcePools/$WORKFORCE_POOL_ID/providers/$WORKFORCE_PROVIDER_ID. For the purpose of this walkthrough, we define them as follows:
| Variable | Value |
|---|---|
WORKFORCE_POOL_ID |
entra-id-oidc-pool-203040 |
WORKFORCE_PROVIDER_ID |
entra-id-oidc-provider |
-
Note that $WORKFORCE_POOL_ID has to be globally unique
resulting in the following redirect URI:
https://auth.cloud.google/signin-callback/locations/global/workforcePools/entra-id-oidc-pool-203040/providers/entra-id-oidc-provider
Fill up the application registration as shown below and click Register.
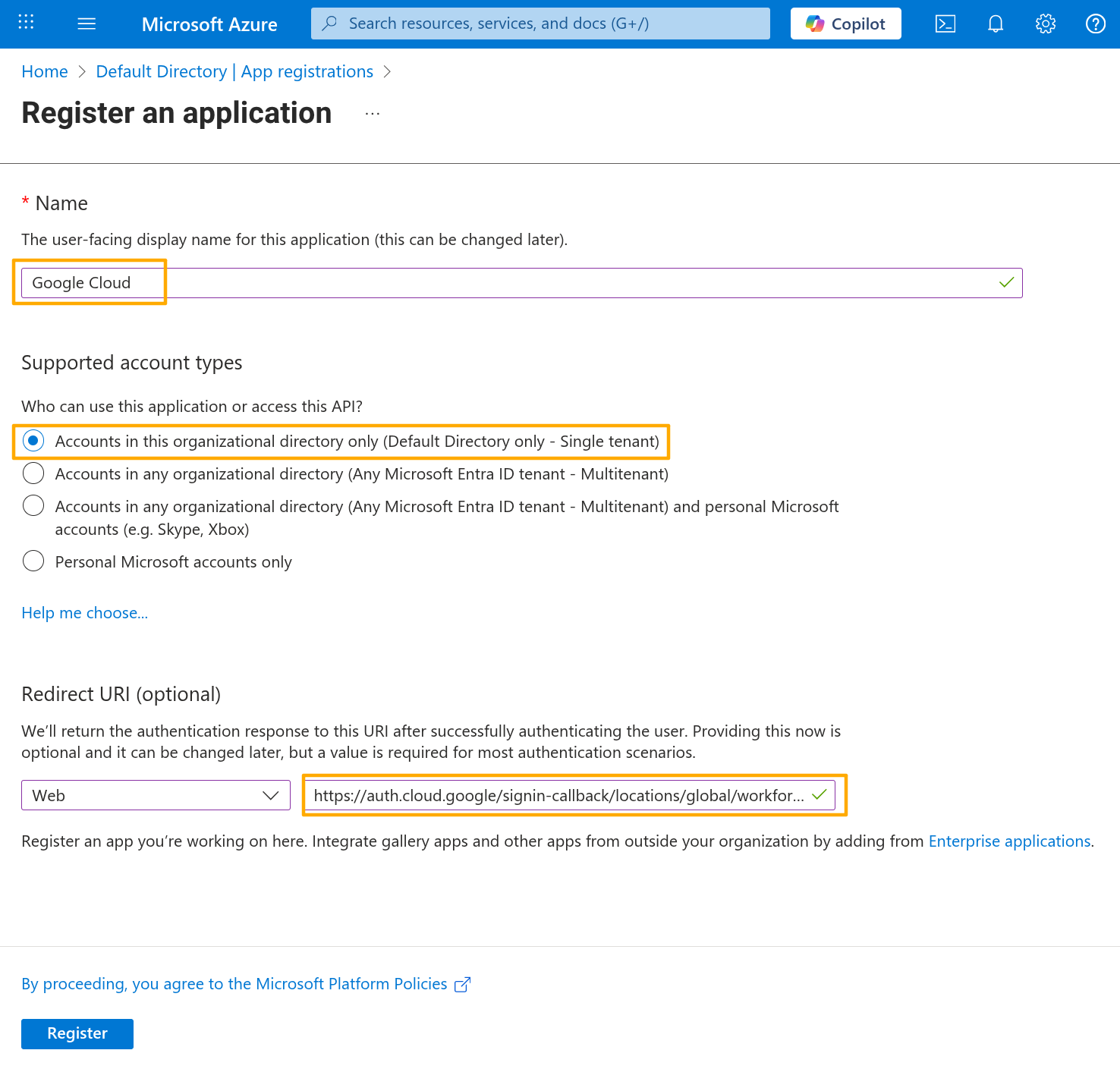
create application secret
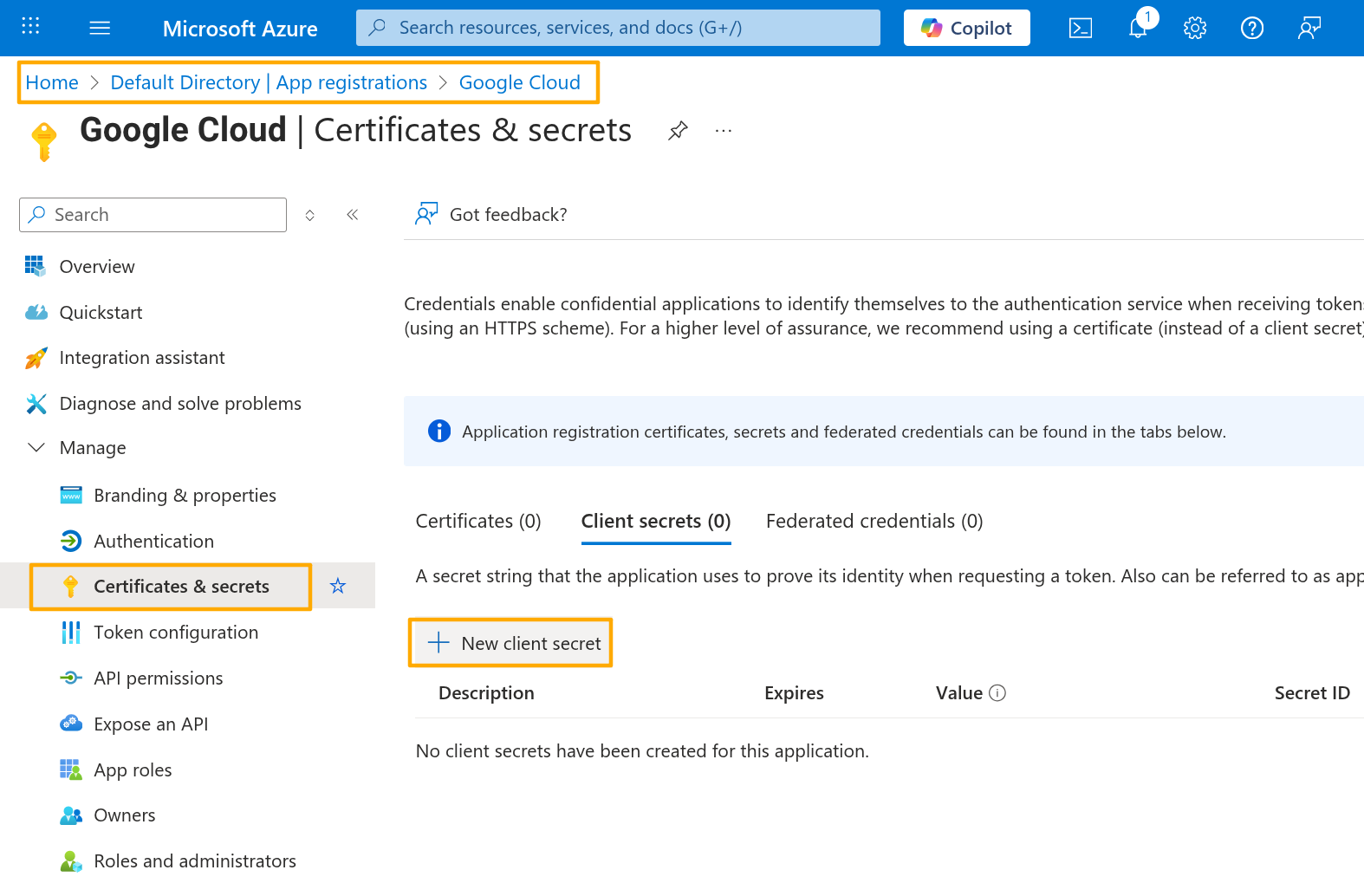
On the Google Cloud application on Entra ID admin, select Certificates and Secrets and click New Client Secret
Create a secret named GoogleCloudWIP.
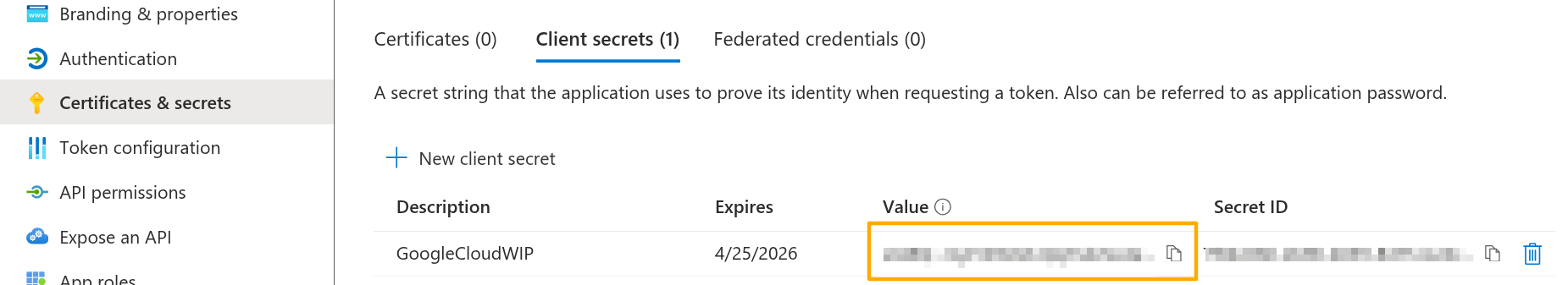
Note the secret value, it will be needed later.
create workforce identity pool on Google Cloud
On Google Cloud console, navigate to IAM & Admin > Workforce Identity Federation. Click on Create Pool and fill in the information below. Note that you need to click Edit to reveal the textbox for the Pool ID. Be sure to select the correct Google Cloud Organization if you have access to multiple Organizations.
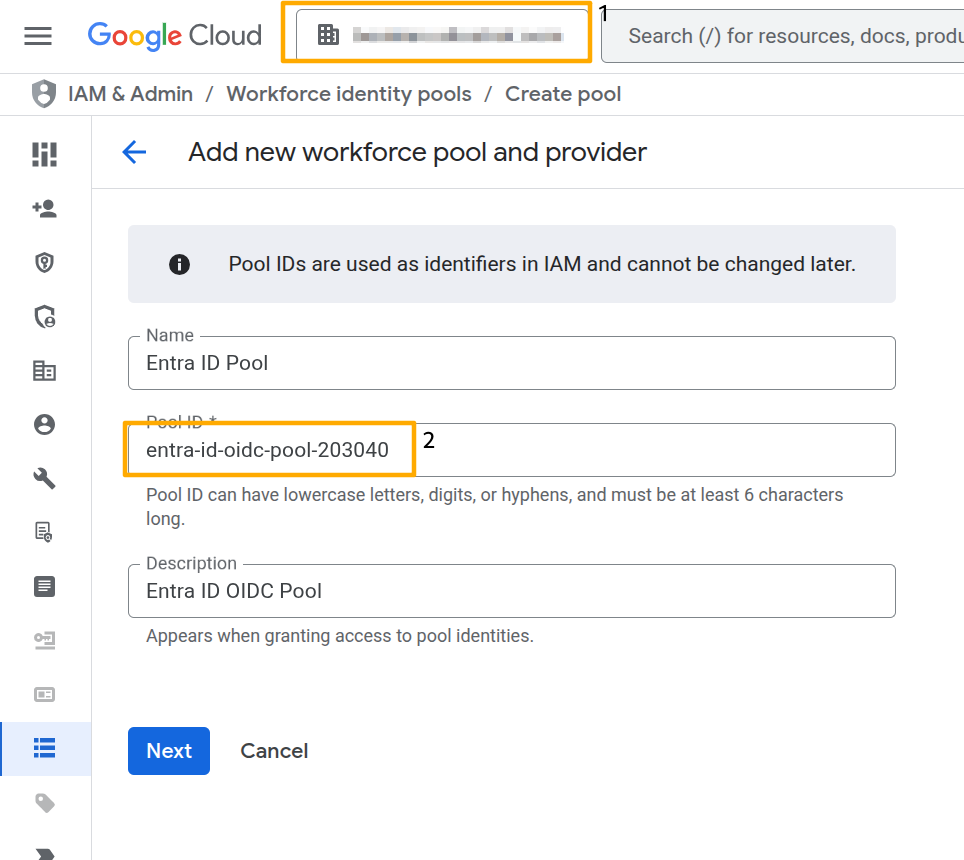
Click Next to continue. You will be prompted to create the Workforce Identity Pool Provider. Select OpenID Connect (OIDC) protocol. We need to provide the Issuer URL and Client ID from Entra ID.
On Entra ID admin, navigate to the Google Cloud Web application we created earlier. You can find the Client ID on the details page.
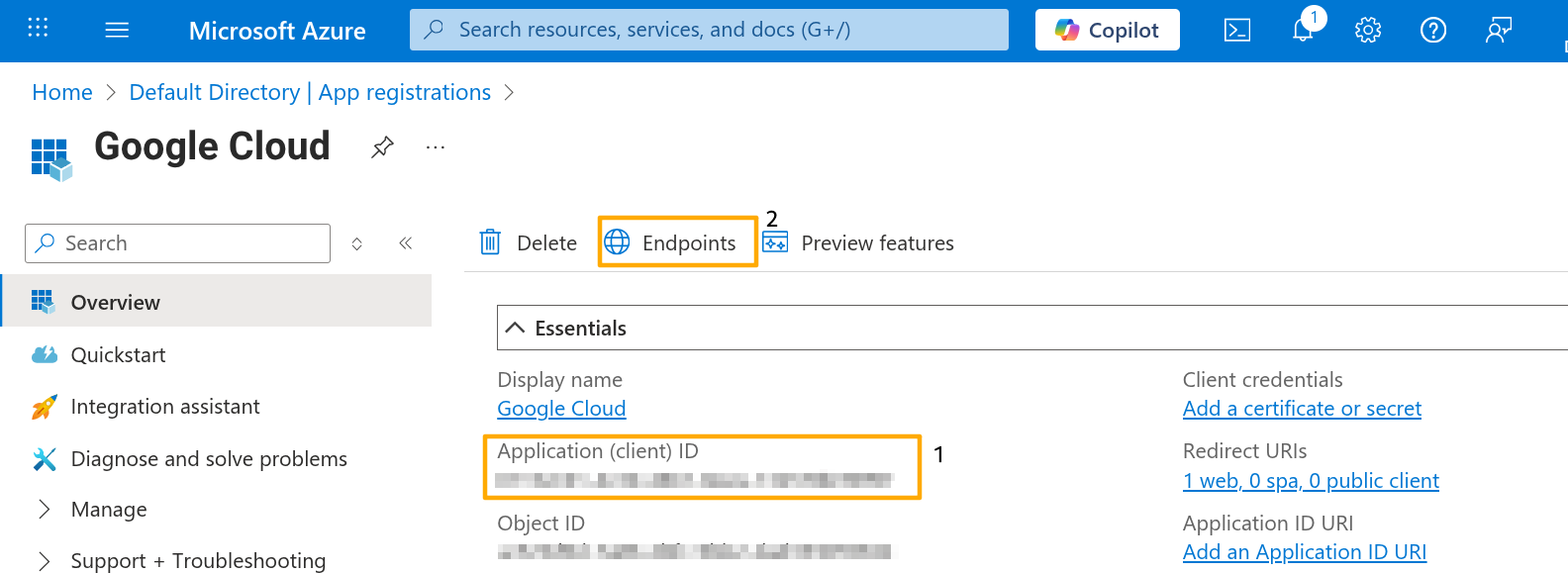
Next, click in Endpoints near the top of the same page.
You will be presented with a list of URLs. Locate the OpenID Connect metadata document on the page and open the corresponding URL in a new browser page. It should be similar to below:
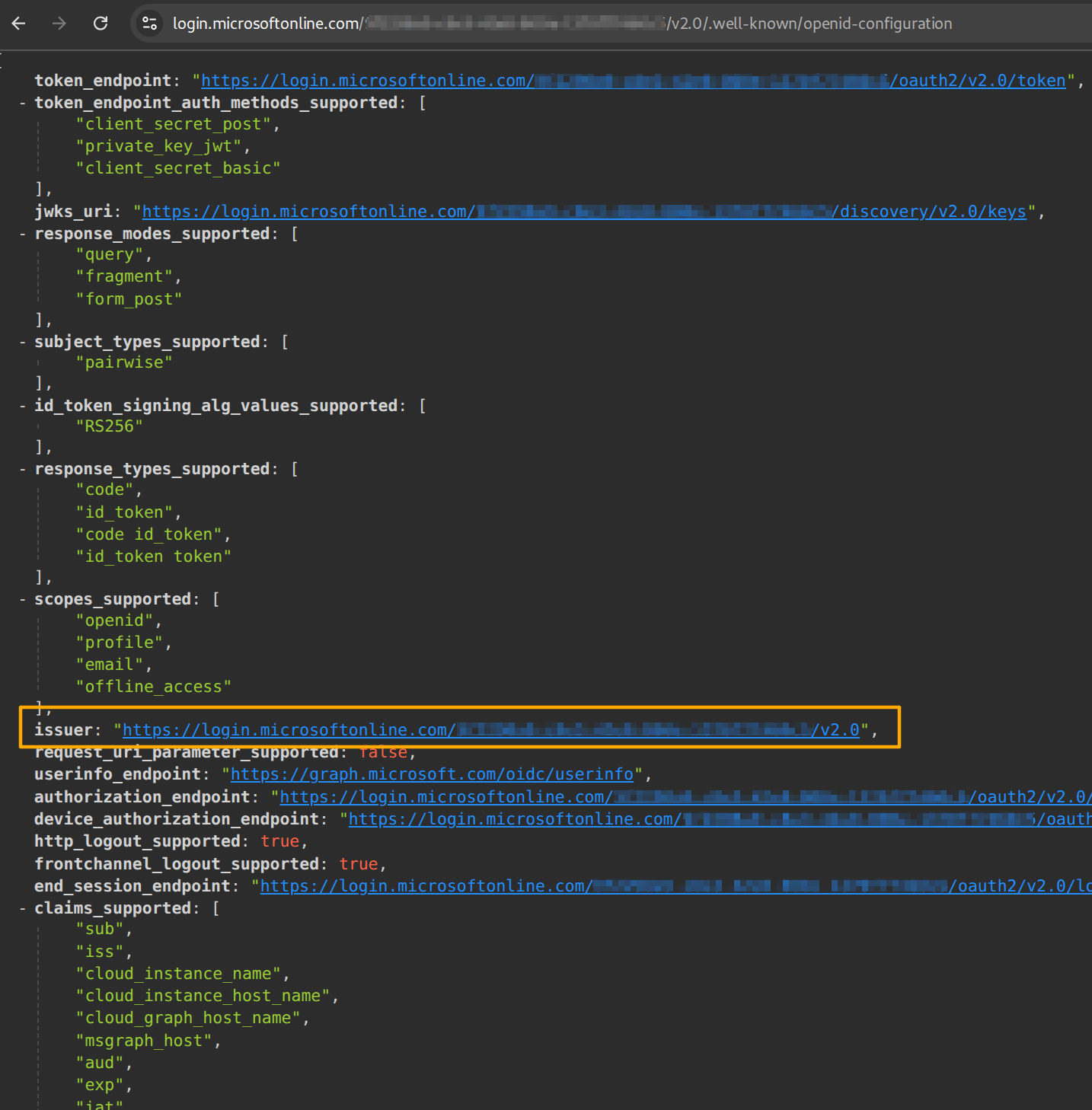
Fill in the information on the Google Cloud create provider page as shown below:
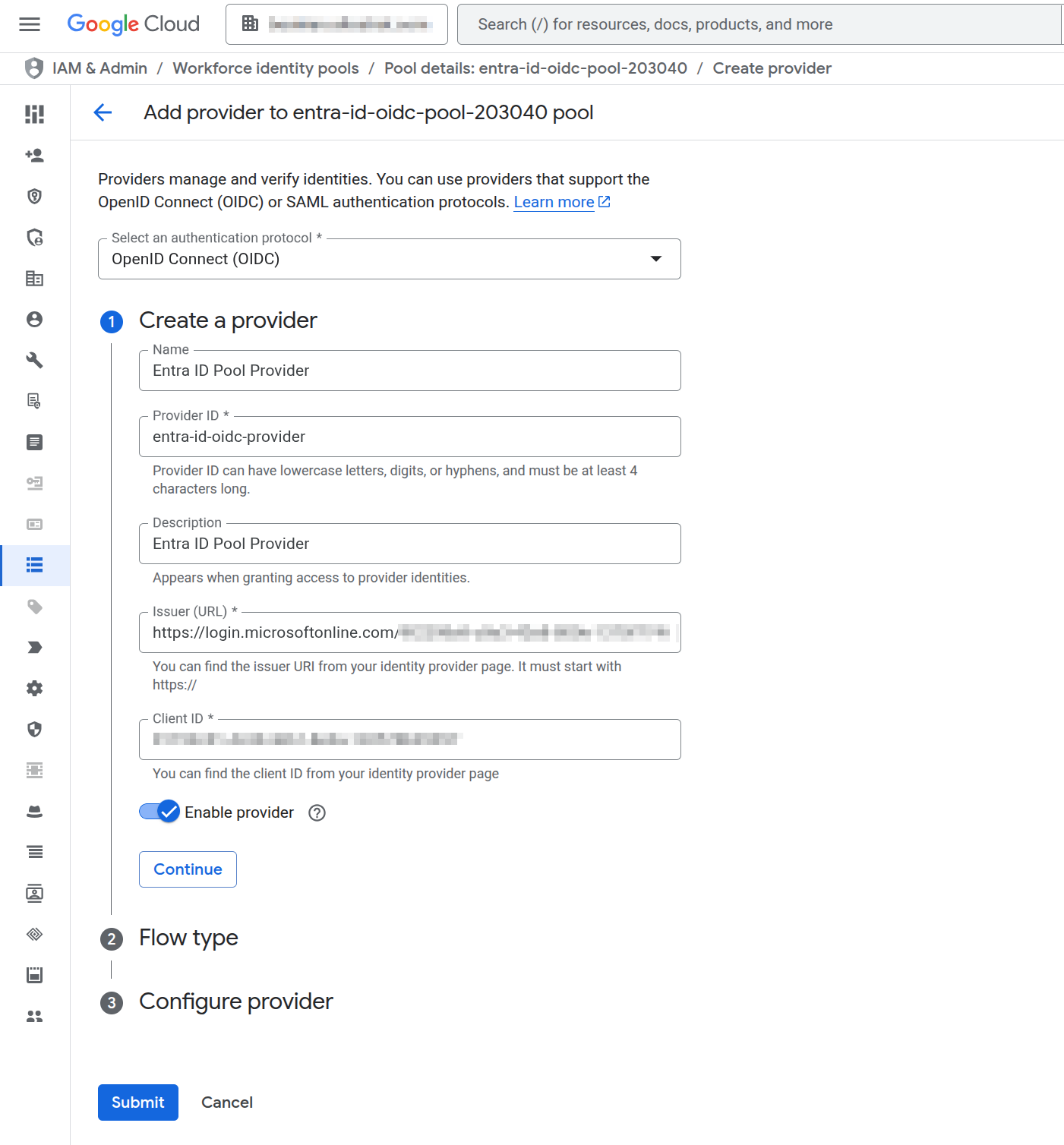
Click Next and fill in the flow type information. The Client Secret is the secret we created on Entra ID above.
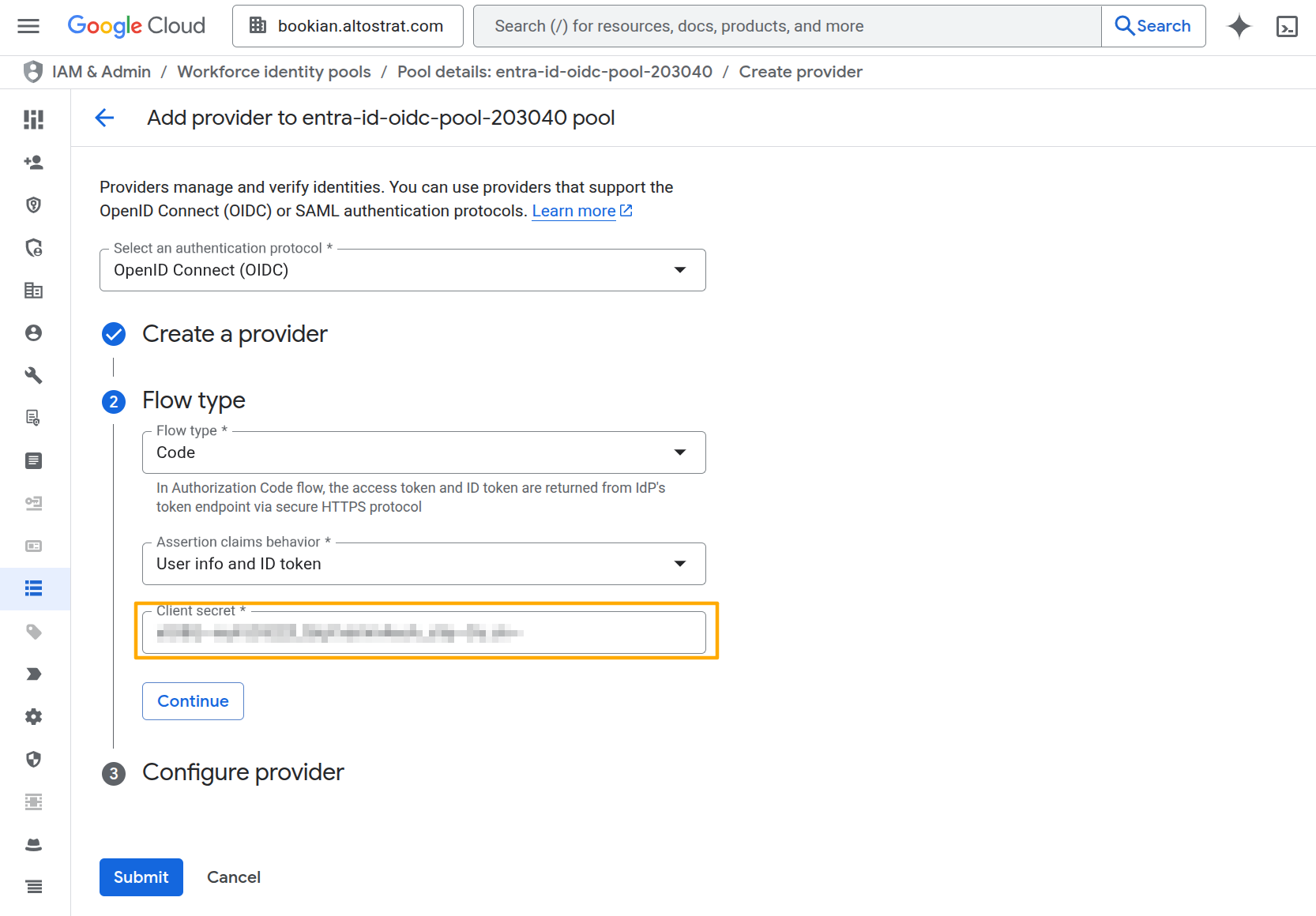
Click Next and fill in the attribute mapping as follows:
| OIDC | |
|---|---|
google.subject |
assertion.email.lowerAscii() |
google.groups |
assertion.groups |
google.display_name |
assertion.given_name |
On Google Cloud Console, it should appear similar to below:
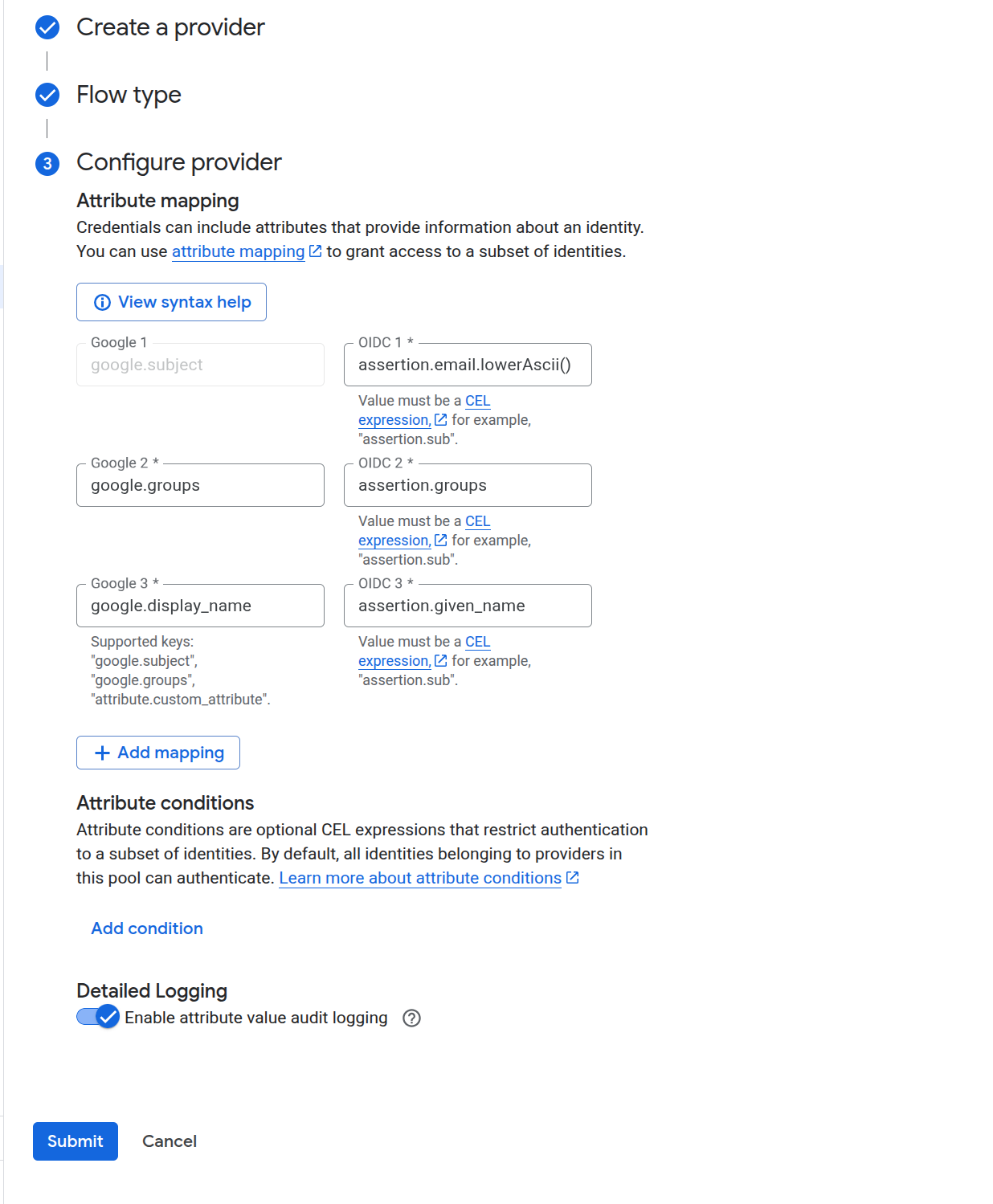
Optionally, enable logging and click Submit
| Note that we are using email as the assertion subject. Therefore it is essential that email is defined for all users that will be accessing Google Cloud resources in Entra ID. |
testing federated access
granting permission
The following table shows the principal identifiers that you use to grant roles to a single user, a group of users, users carrying a particular claim, or all users from a workforce pool.
Identities |
Identifier format |
Single identity in a workforce identity pool |
principal://iam.googleapis.com/locations/global/workforcePools/POOL_ID/subject/SUBJECT_ATTRIBUTE_VALUE |
All workforce identities in a group |
principalSet://iam.googleapis.com/locations/global/workforcePools/POOL_ID/group/GROUP_ID |
All workforce identities with a specific attribute value |
principalSet://iam.googleapis.com/locations/global/workforcePools/POOL_ID/attribute.ATTRIBUTE_NAME/ATTRIBUTE_VALUE |
All identities in a workforce identity pool |
principalSet://iam.googleapis.com/locations/global/workforcePools/POOL_ID/* |
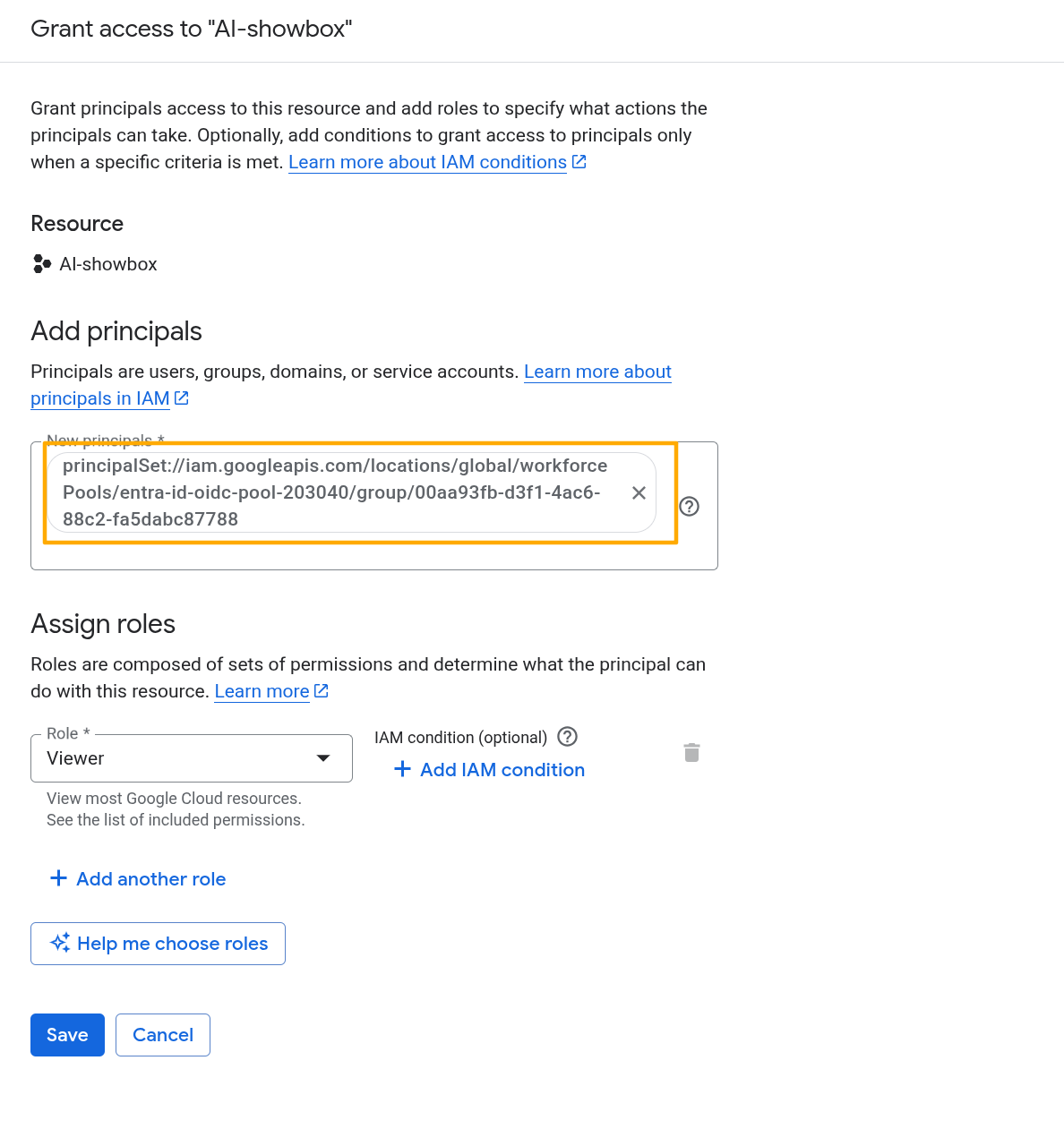
As an example, we’ll create an IAM access policy for a group. As above, the format is principalSet://iam.googleapis.com/locations/global/workforcePools/POOL_ID/group/GROUP_ID. The GROUP_ID is the Entra ID group’s Object ID.
On Google Cloud console, navigate to the IAM page of the specific project.
signing in
With the permission granted, we can now navigate to the sign in URL. You can find the sign in URL on the Workforce Identity Pool details page:
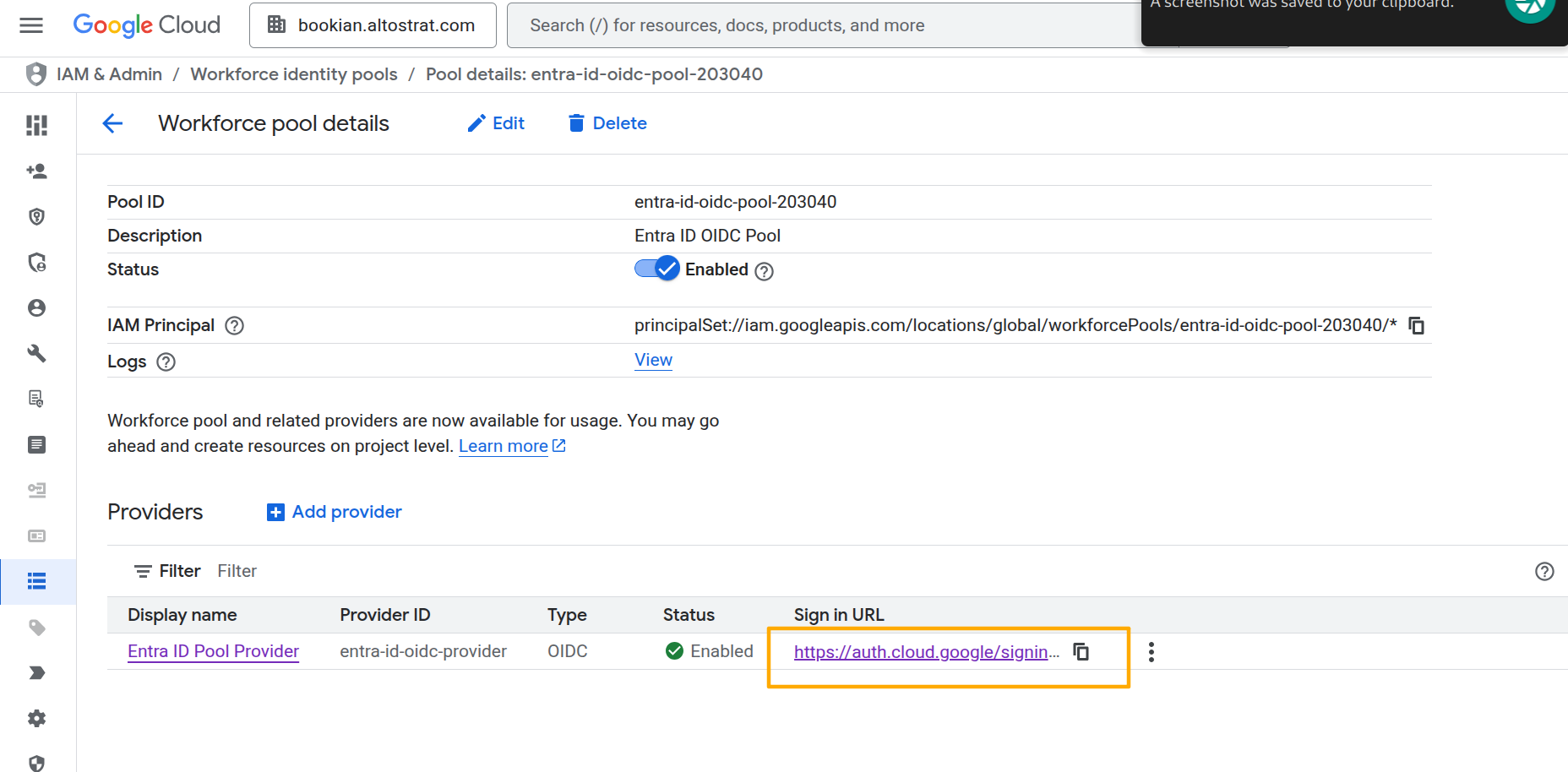
Copy the URL and paste it in a new browser tab. You should be redirected to login via your Entra ID, and you should be directed back to Google Cloud console upon successful login.
Confirm your credentials by clicking on the icon on the top-right of the console.
how to do this using the command line?
I demonstrated creating WIP using the console. Please refer to official documentation on how to perform the same task using the gcloud CLI.
wrap up
In this post, you learned how to configure Workforce Identity Federation between Google Cloud and Microsoft Entra ID. This allows you to leverage your existing identity provider to manage access to Google Cloud resources, streamlining user management and improving security. By following these steps, you have enabled a seamless and secure single sign-on (SSO) experience for your users, allowing them to access Google Cloud with their familiar Entra ID credentials.