A digital native customer recently approached me to help them align their identity management for they multi-cloud (Google Cloud and AWS) environments. The goal is to use a single identity provider to sign in to both AWS and Google Cloud. They are already using Google Workspace (GWS) as their collaboration and productivity suite, and as the identity provider for Google Cloud access. Therefore it most sense to also use GWS as the IDP for AWS.
Unlike on Google Cloud, where organization resources and Identity and Acccess Management (IAM) have a hierarchical structure, it is common, and a best practice, to have AWS resources in multiple accounts. The trouble is, each account has it’s own IAM. This makes managing accounts more complicated and troublesome. AWS’s solution to this is the Identity Center (formerly AWS SSO). Identity Center allows users to access multiple accounts using a single credential, and it supports external identity providers such as Google Workspace.
Here are the steps to enable AWS Identity Center integration with Google Workspace.
create GWS application
The first step is to create a Google Workspace (or Cloud Identity) "App". In this context, the App is a connected service that allow your users to sign in with their managed Google account. There are pre-configured templates for common apps, and AWS is one of them.
To begin, open the admin console to add an app. Search for Amazon Web Services
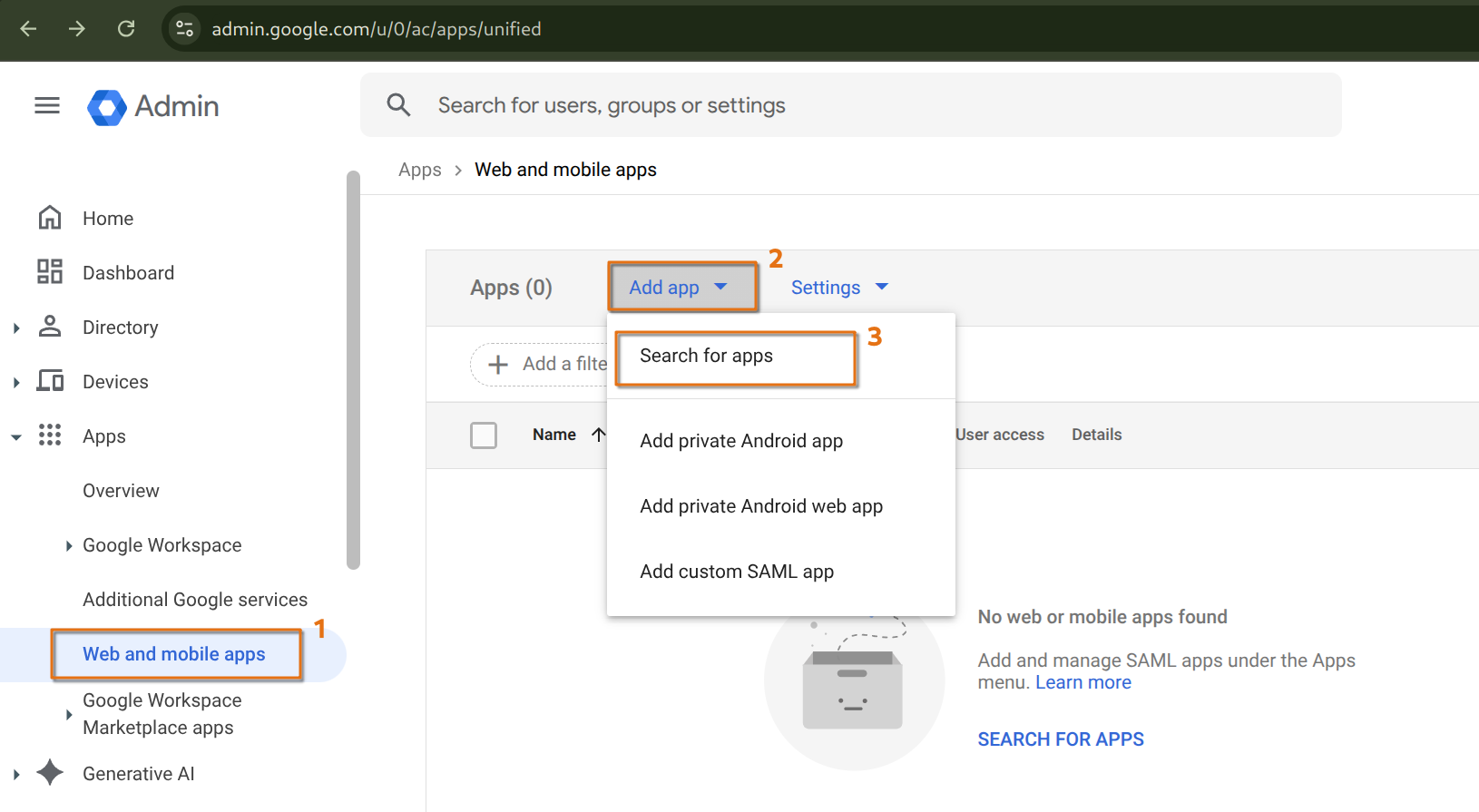
and download the metadata
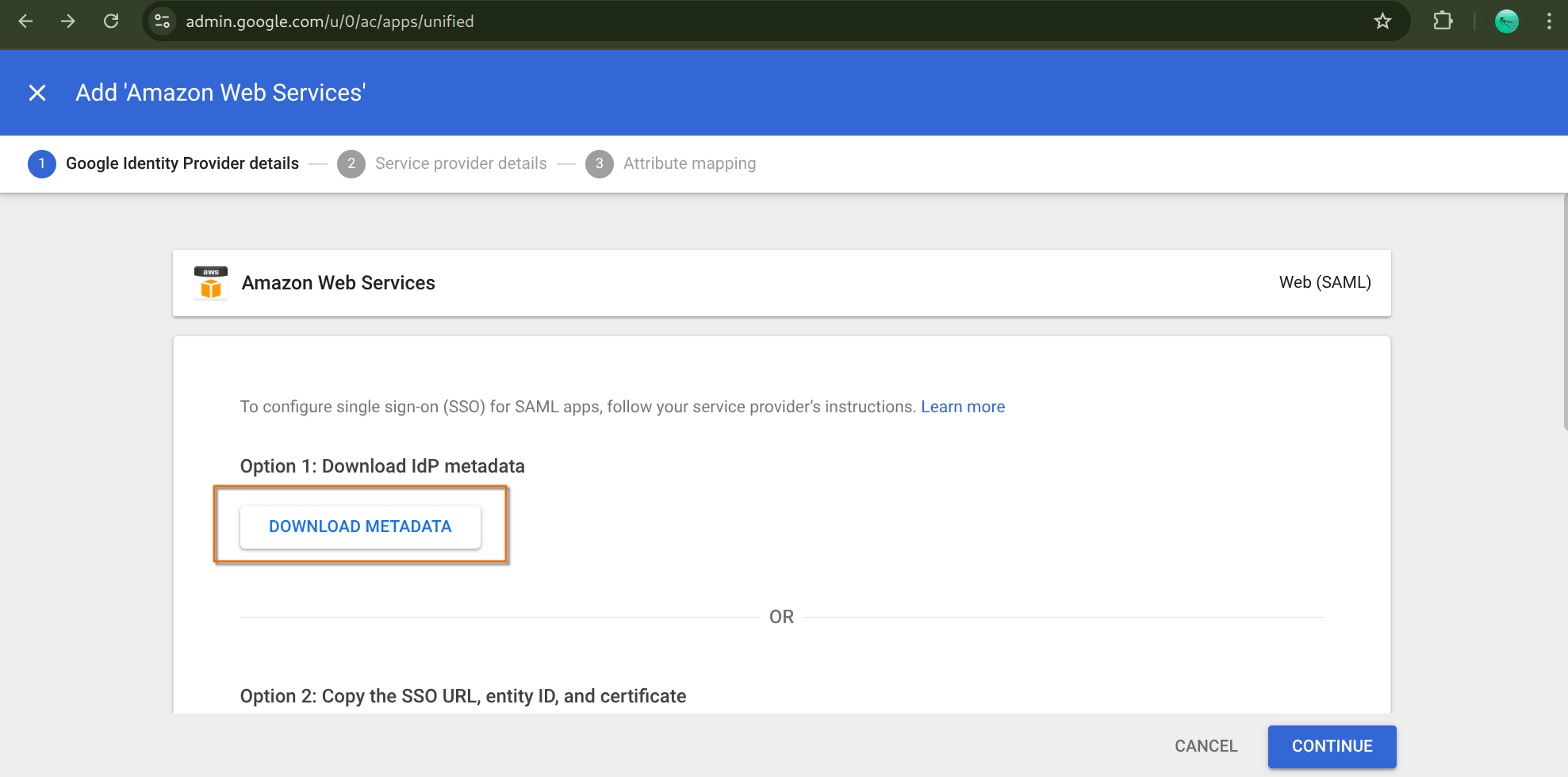
leave the admin console open, we’ll come back to it later. Now open a new browser tab for the AWS end.
enable IAM identity center
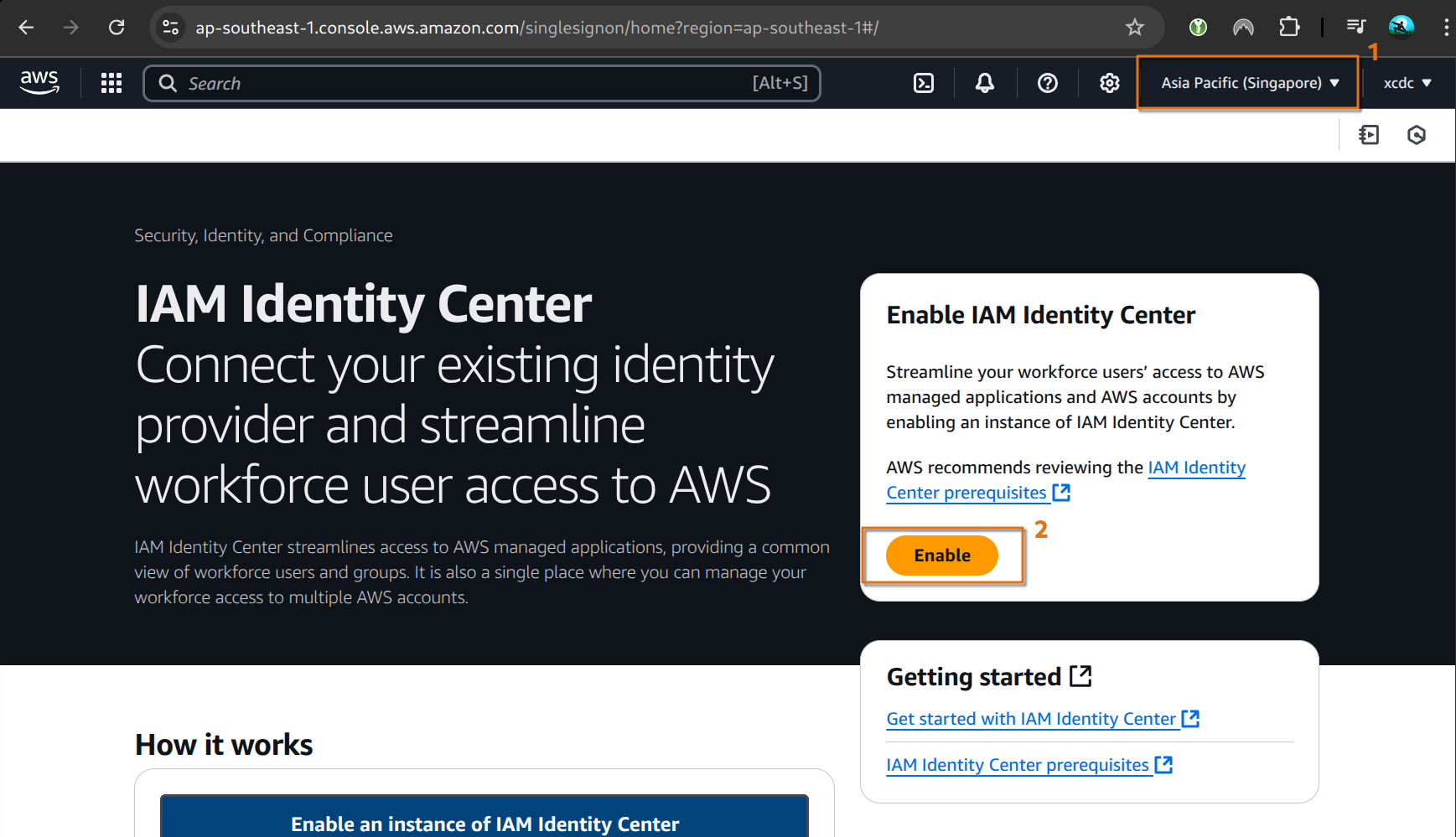
On the AWS console, navigate to the Identity Center page. Ensure that you select the primary region before enabling the service.
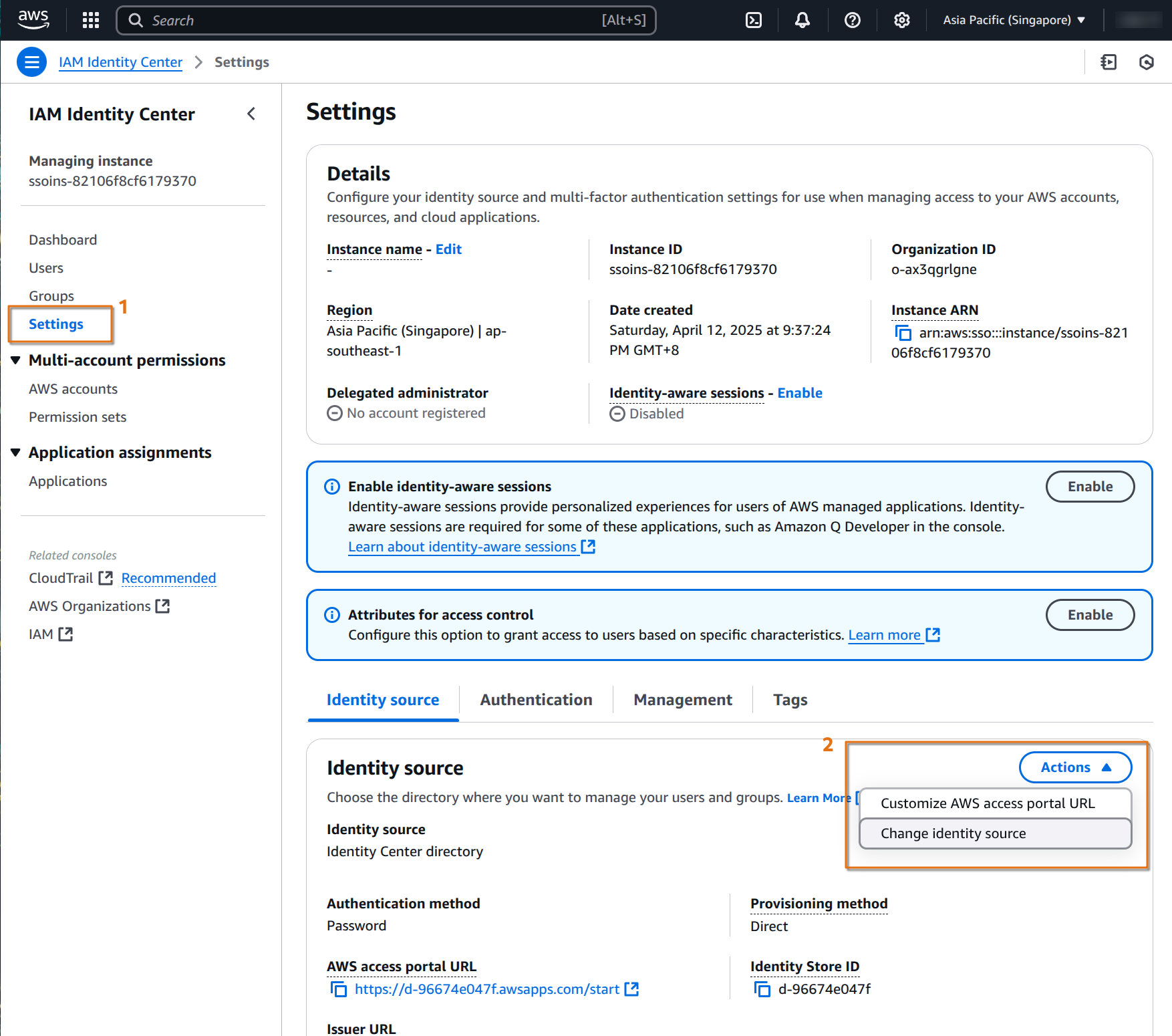
change identity source
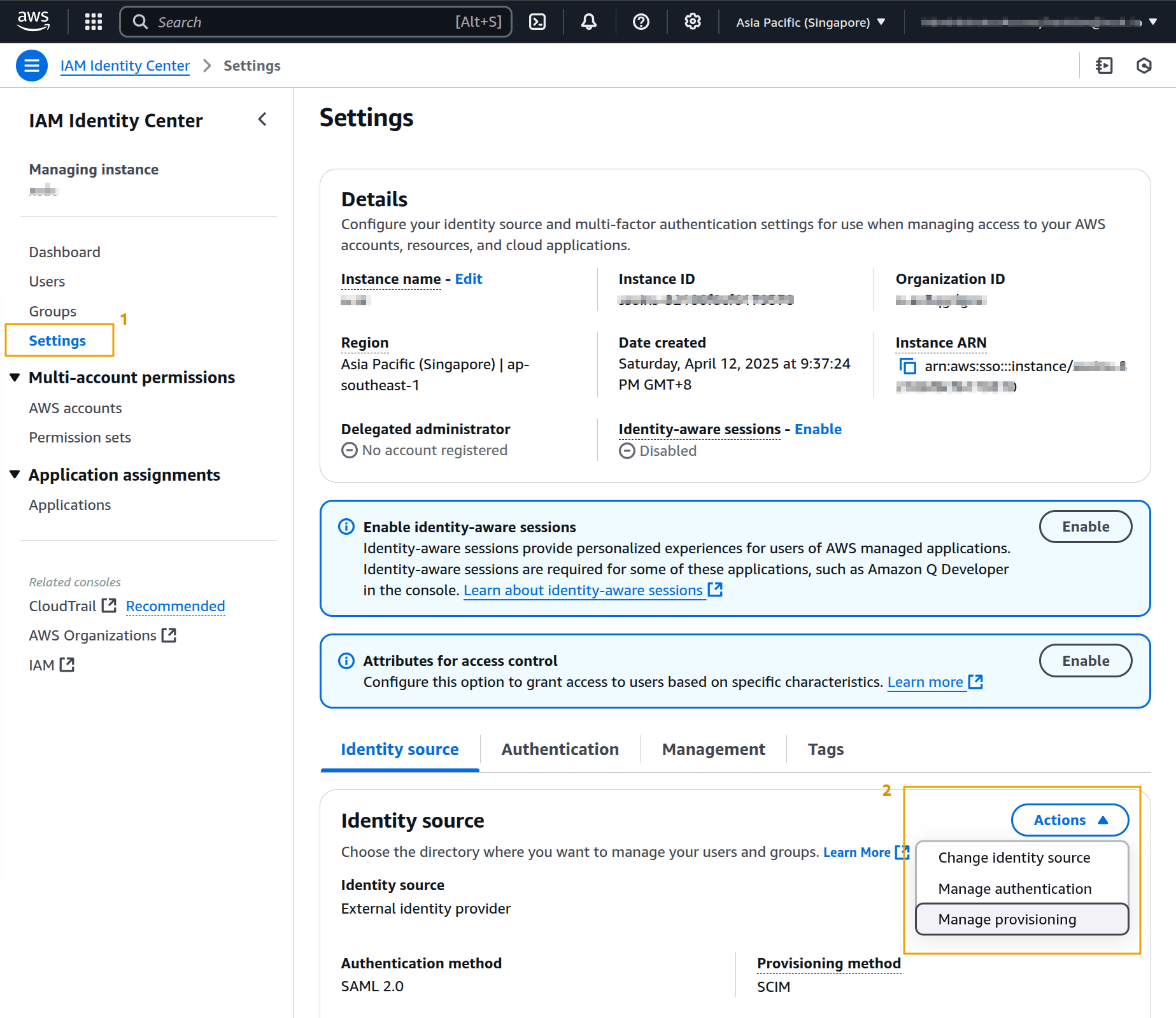
Next, go into the Settings section and select Change identity source under the Action menu
Here, you want to configure External identity provider
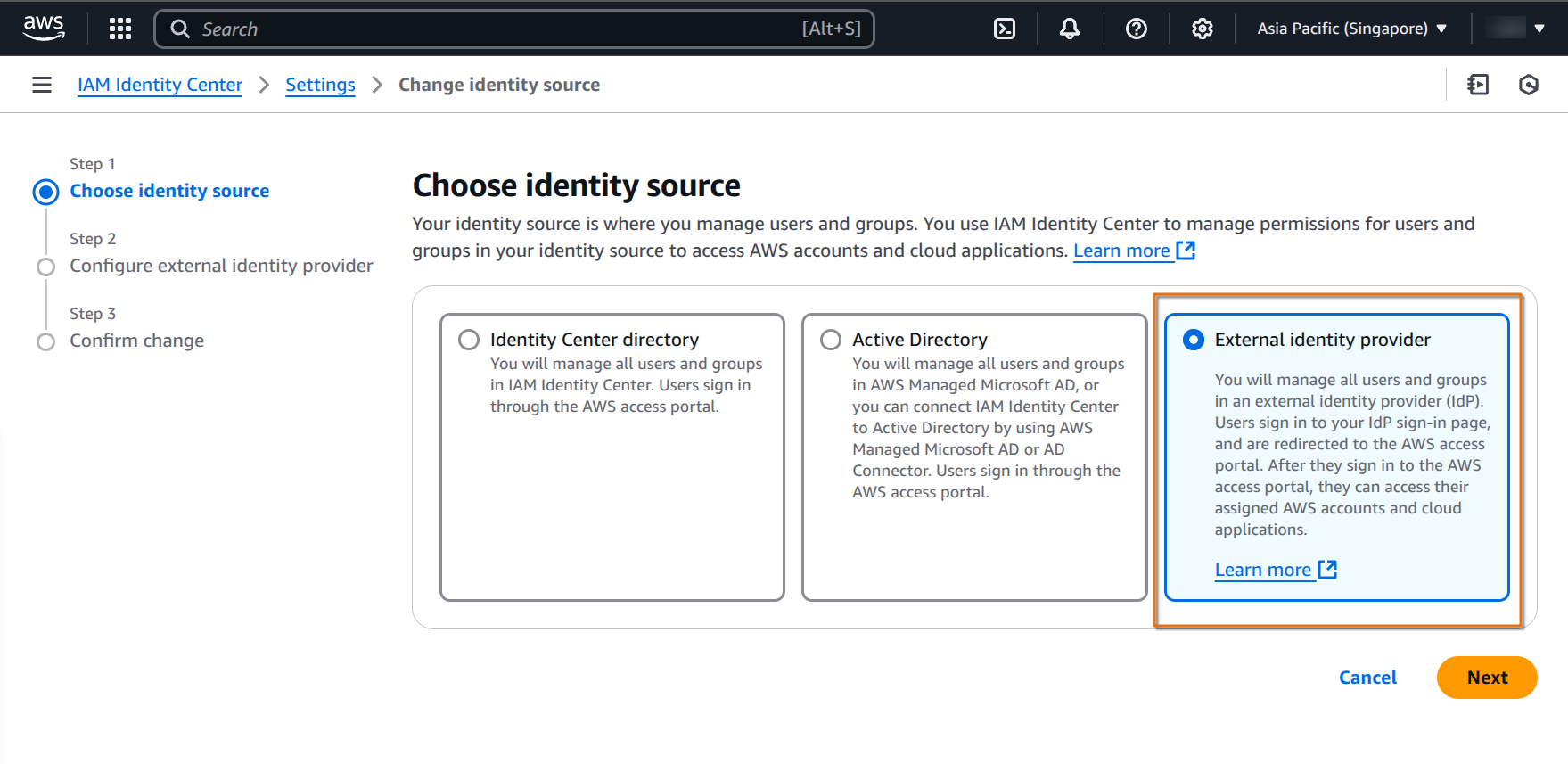
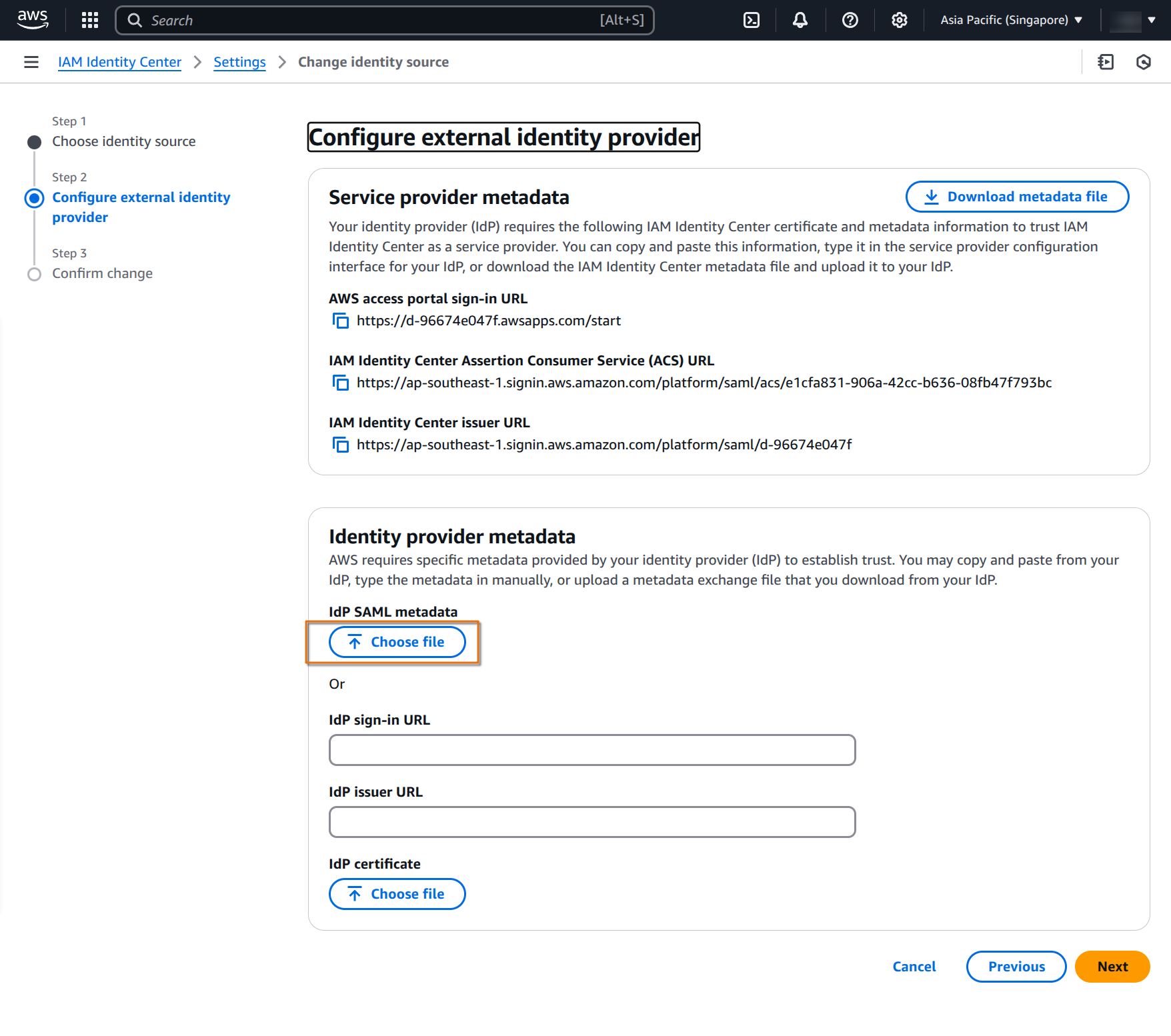
and upload the metadata file we downloaded from the Google Workspace / Cloud Identity console
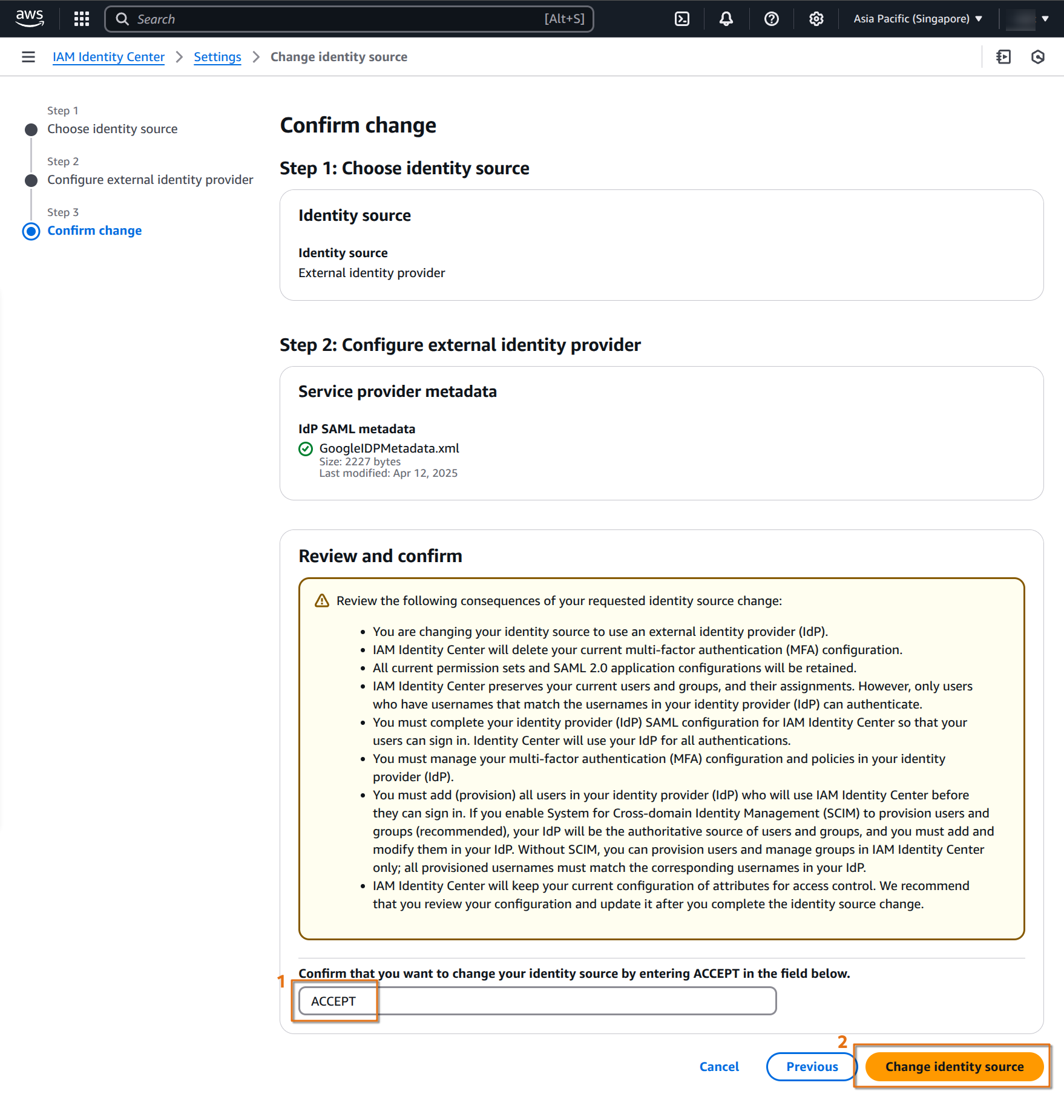
review, and confirm
mapping the SAML urls
After we changed the identity source, go to Settings and select Manage authentication from the Actions menu.
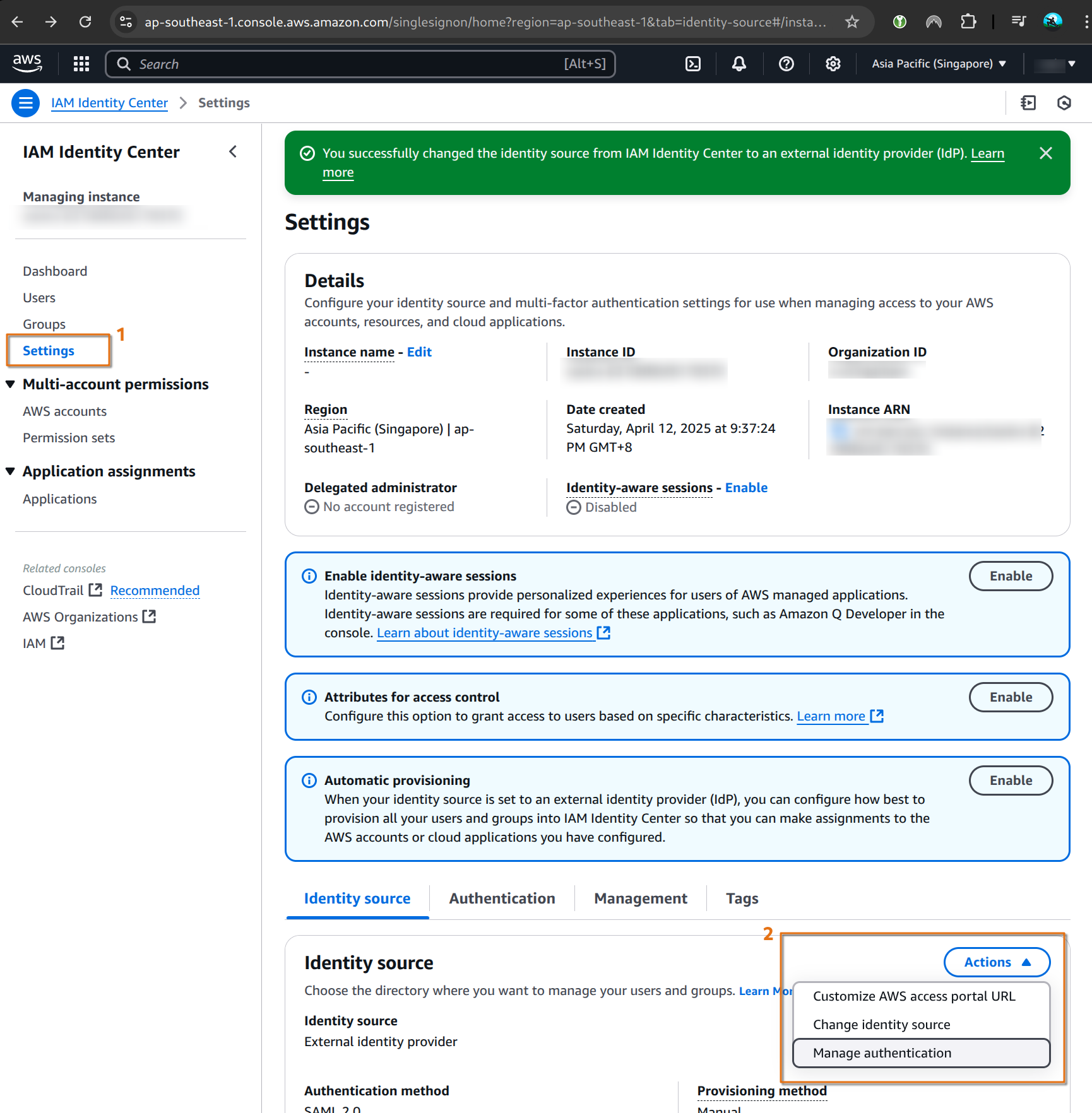
this will bring up the page with a couple of URLs that we’ll use to configure the Google end:
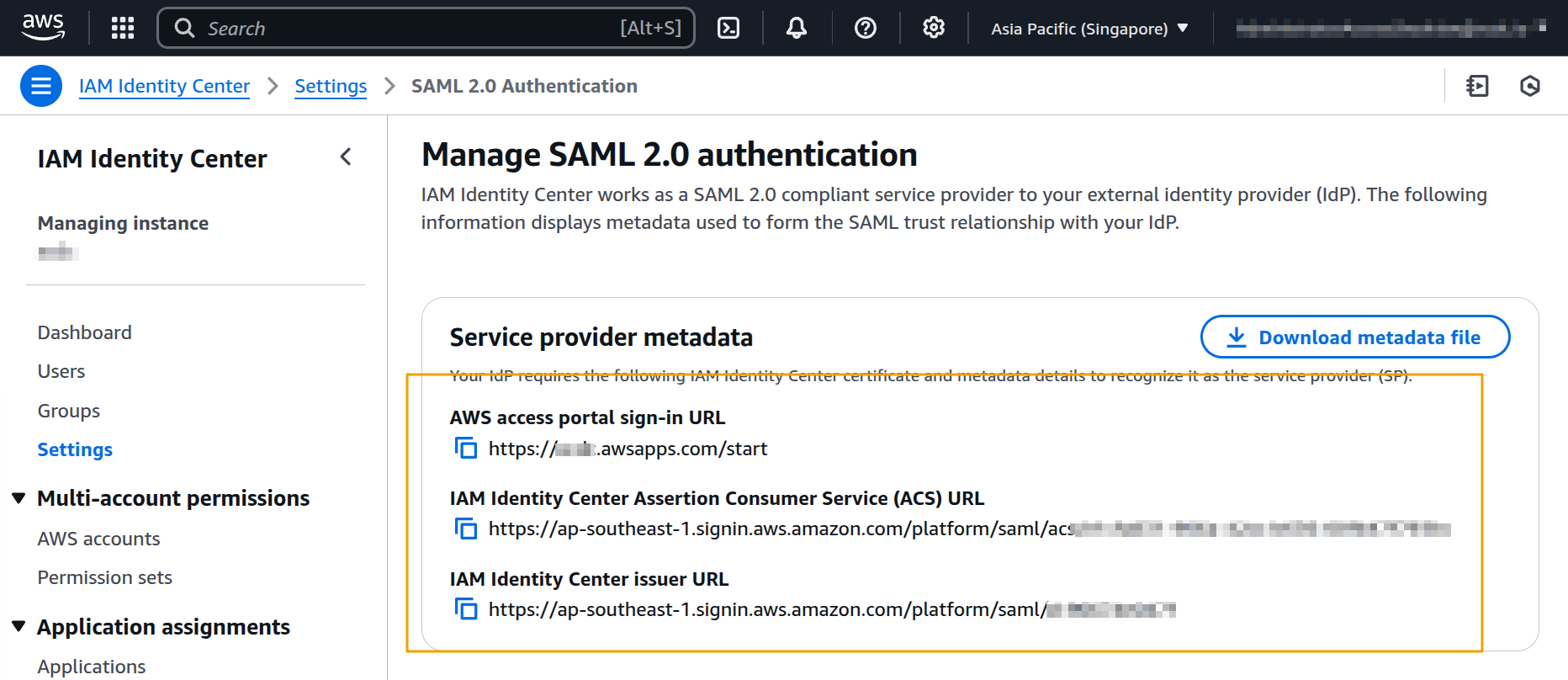
AWS and Google Workspace uses different terms for the URLs, below is the mapping
| AWS | Google Workspace |
|---|---|
AWS access portal sign-in URL |
Start URL |
IAM Identity Center Assertion Consumer Service (ACS) URL |
ACS URL |
IAM Identity Center issuer URL |
Entity ID |
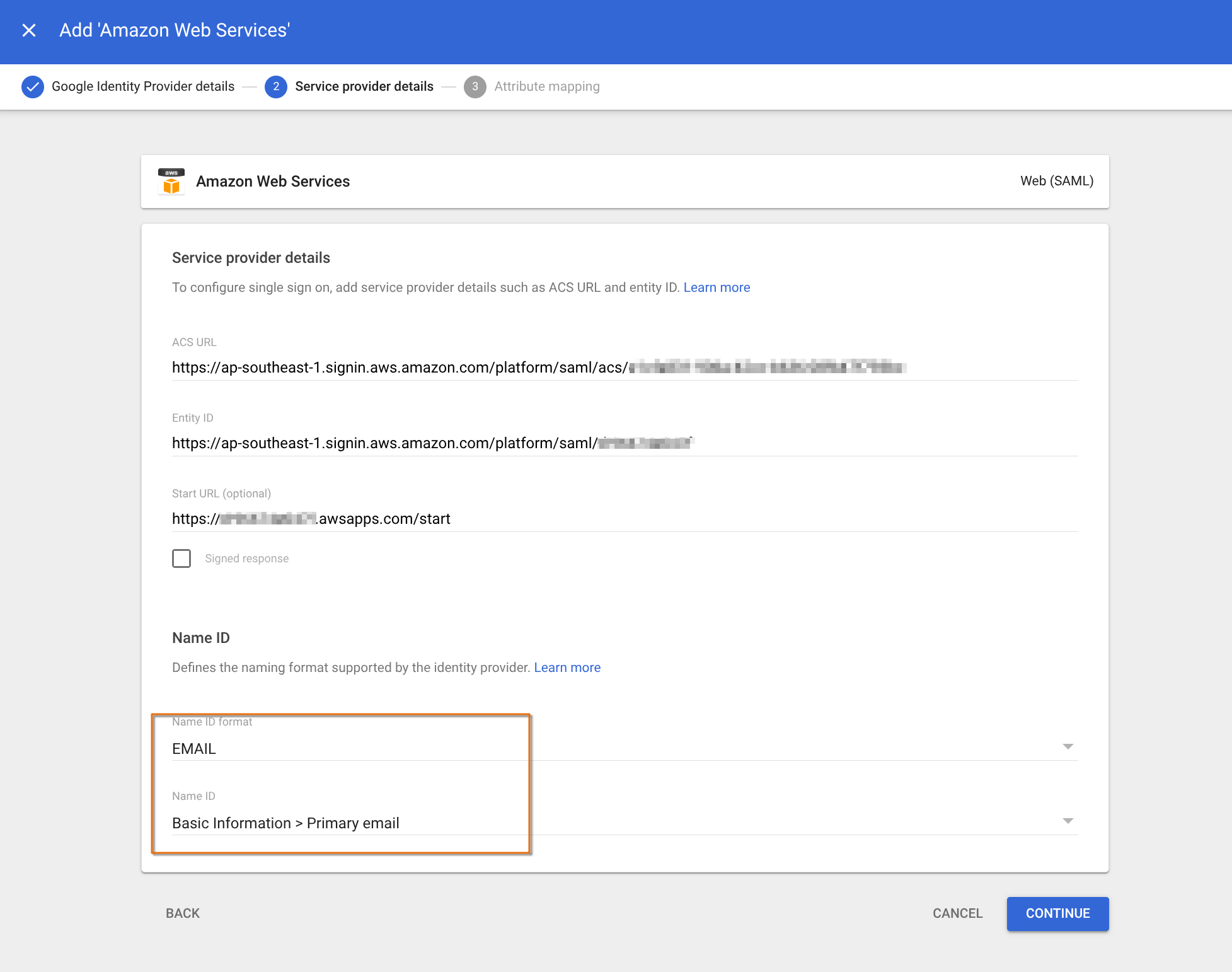
Populate the URLs on the GWS admin console
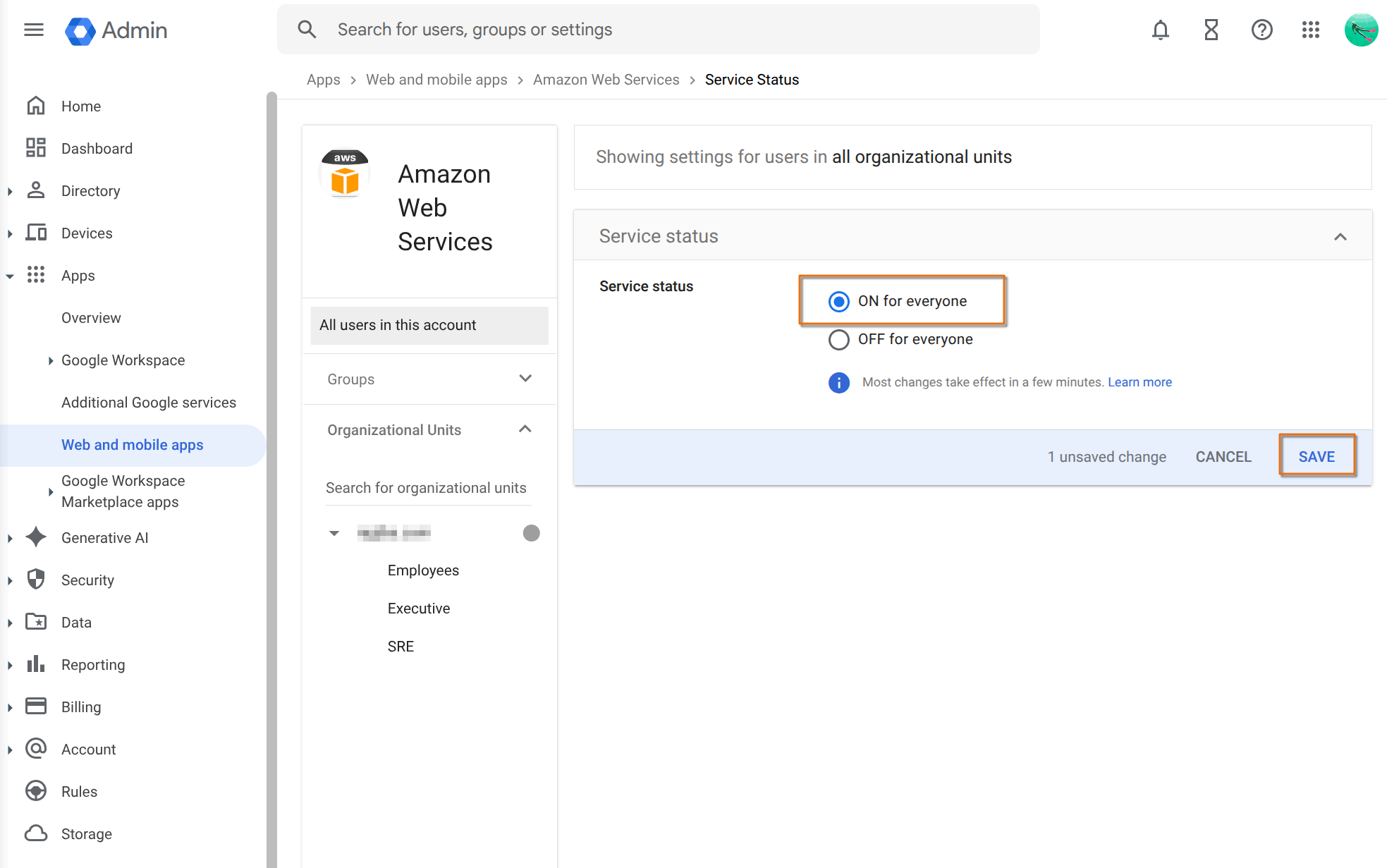
Next, configure which group of users can access the AWS Identity Center. In the example below, I’ve enabled for everyone in the organization.
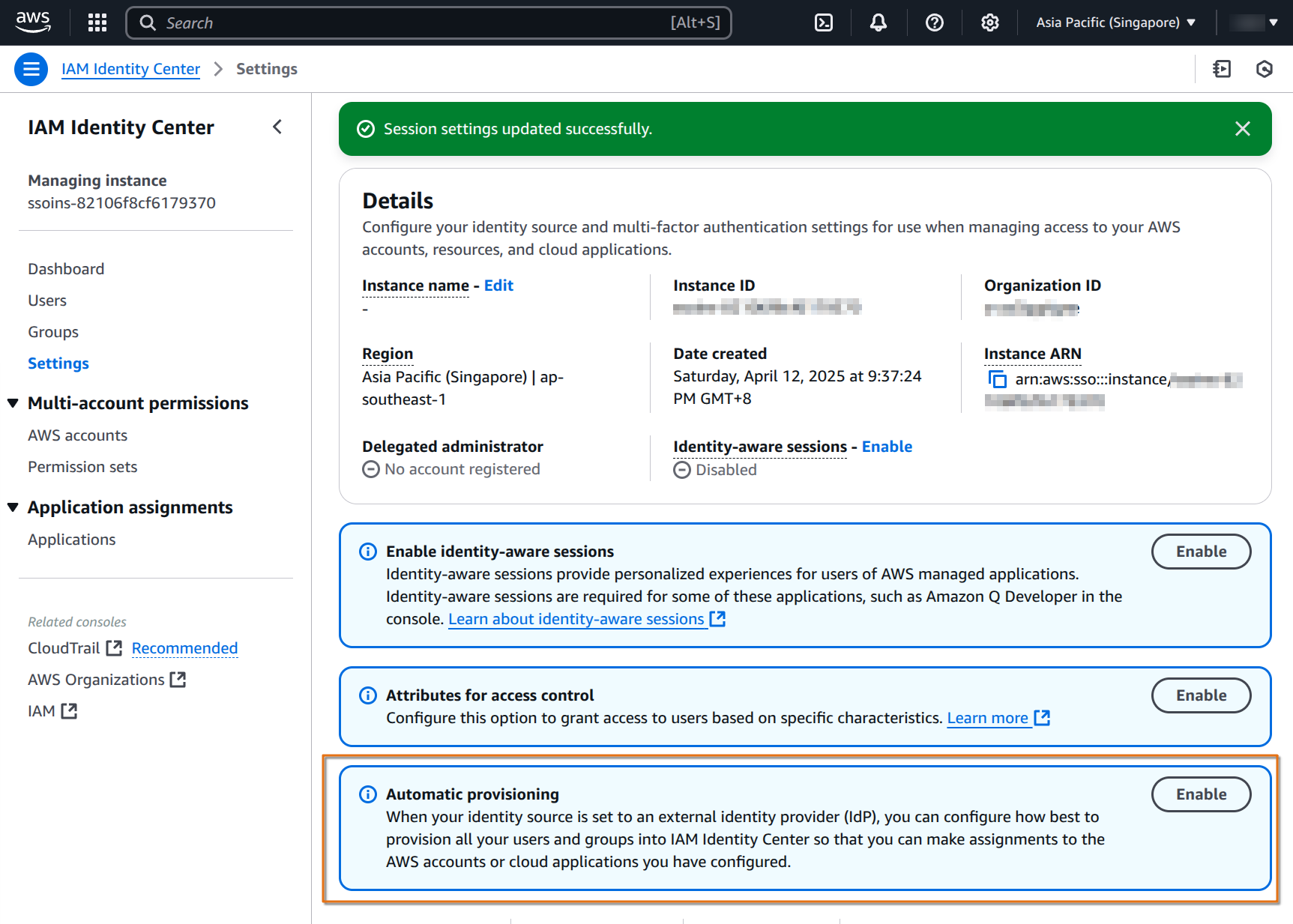
automatic provisioning
Auto provisioning allows automatic synchronization of user information from Google Workspace to Identity Center. Changes made in Google directory are automatically reflected in IAM Identity Center.
On the AWS console, enable Automatic provisioning
A popup page will show the SCIM endpoint and Access token information. Copy them down.
If you close the page, you can find those information by selecting Manage provisioning on the settings page
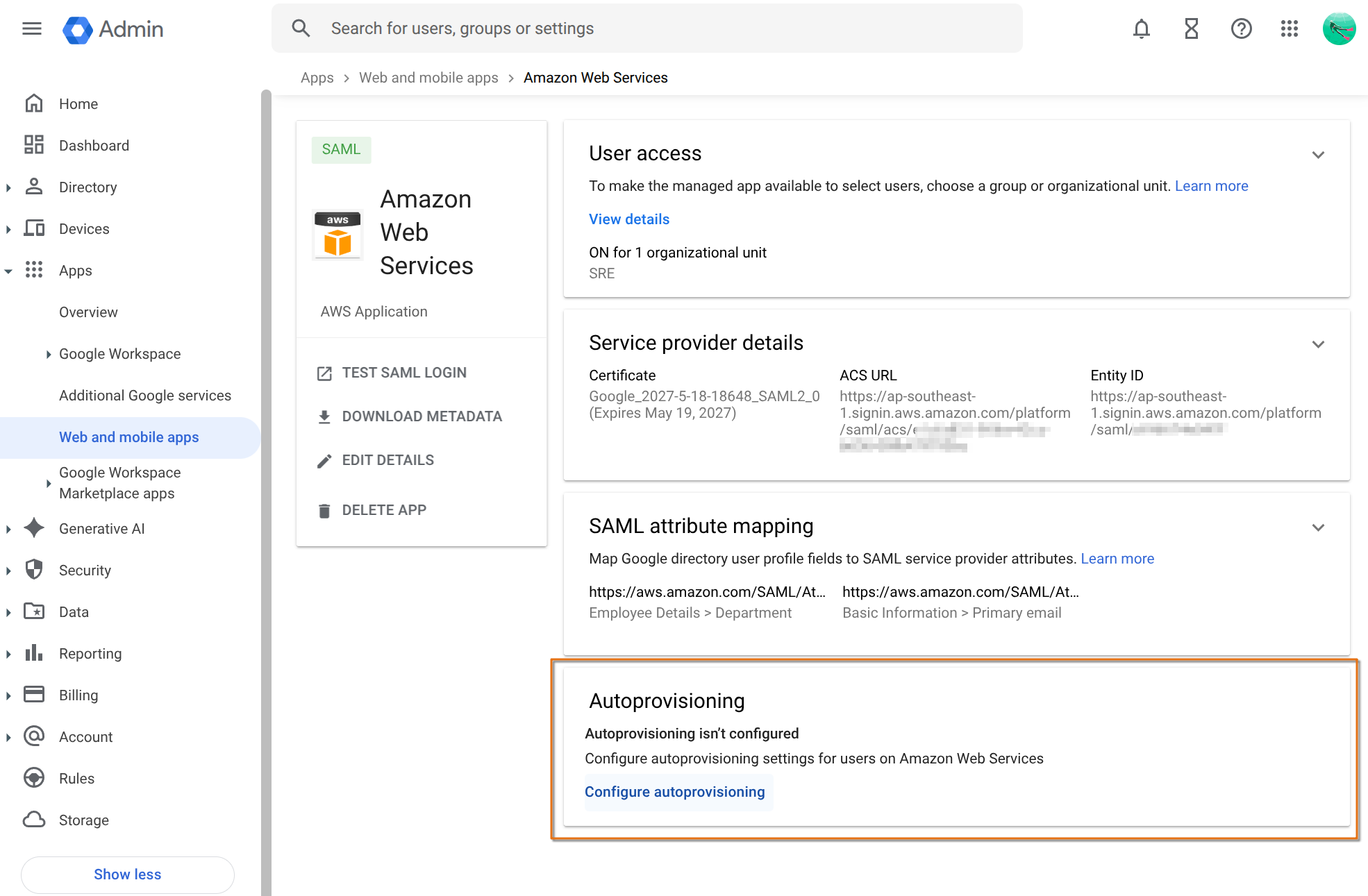
On the GWS admin, select Configure autoprovisioning
Fill in the SCIM Endpoint and Access Token information, and verify the attribute mapping between Identity Center and Google Directory.
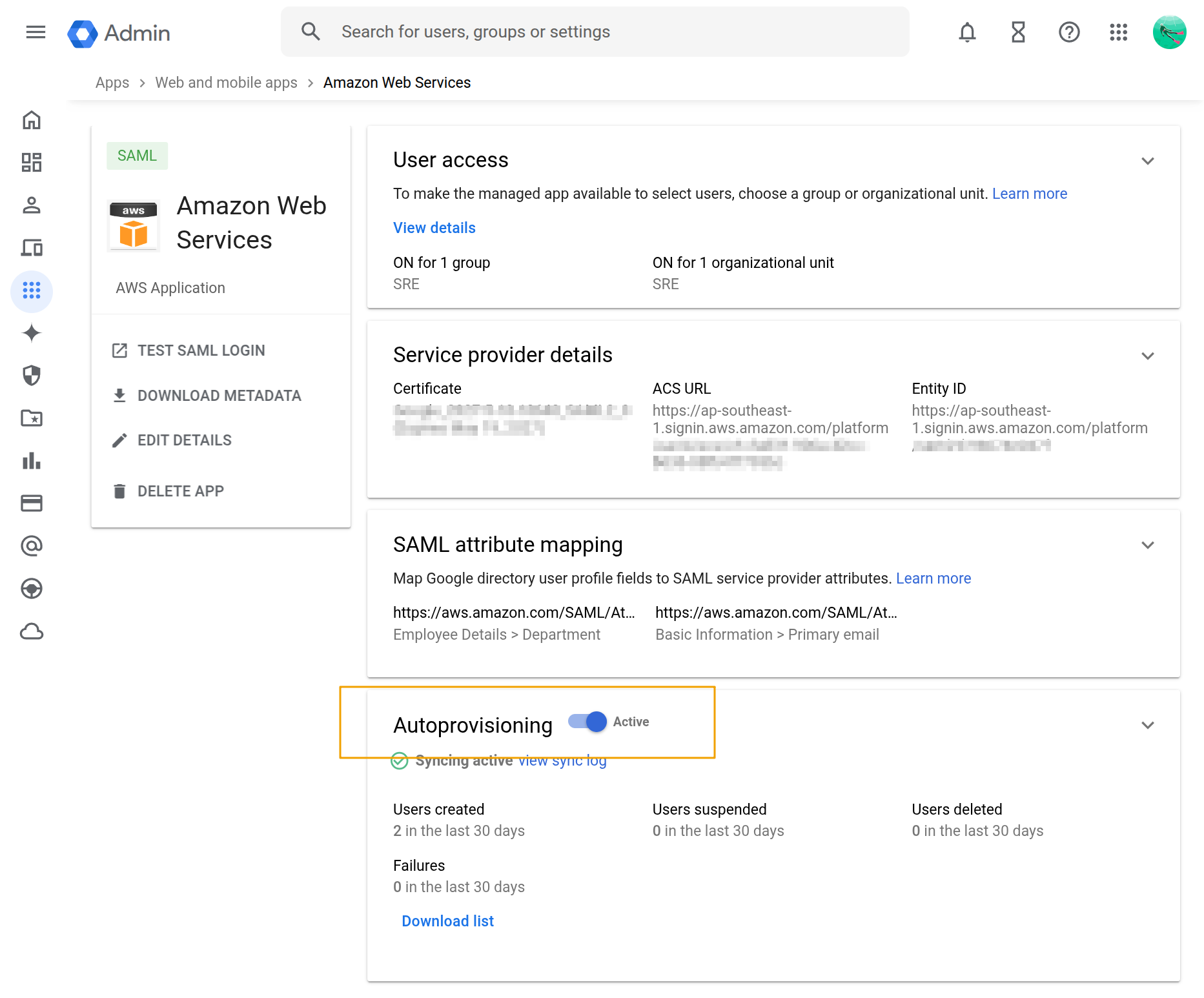
Verify and adjust the deprovisioning settings and finally ensure that Autoprovisioning toggle is on
login
On AWS console, locate the AWS access portal URL on the IAM Identity Center settings page
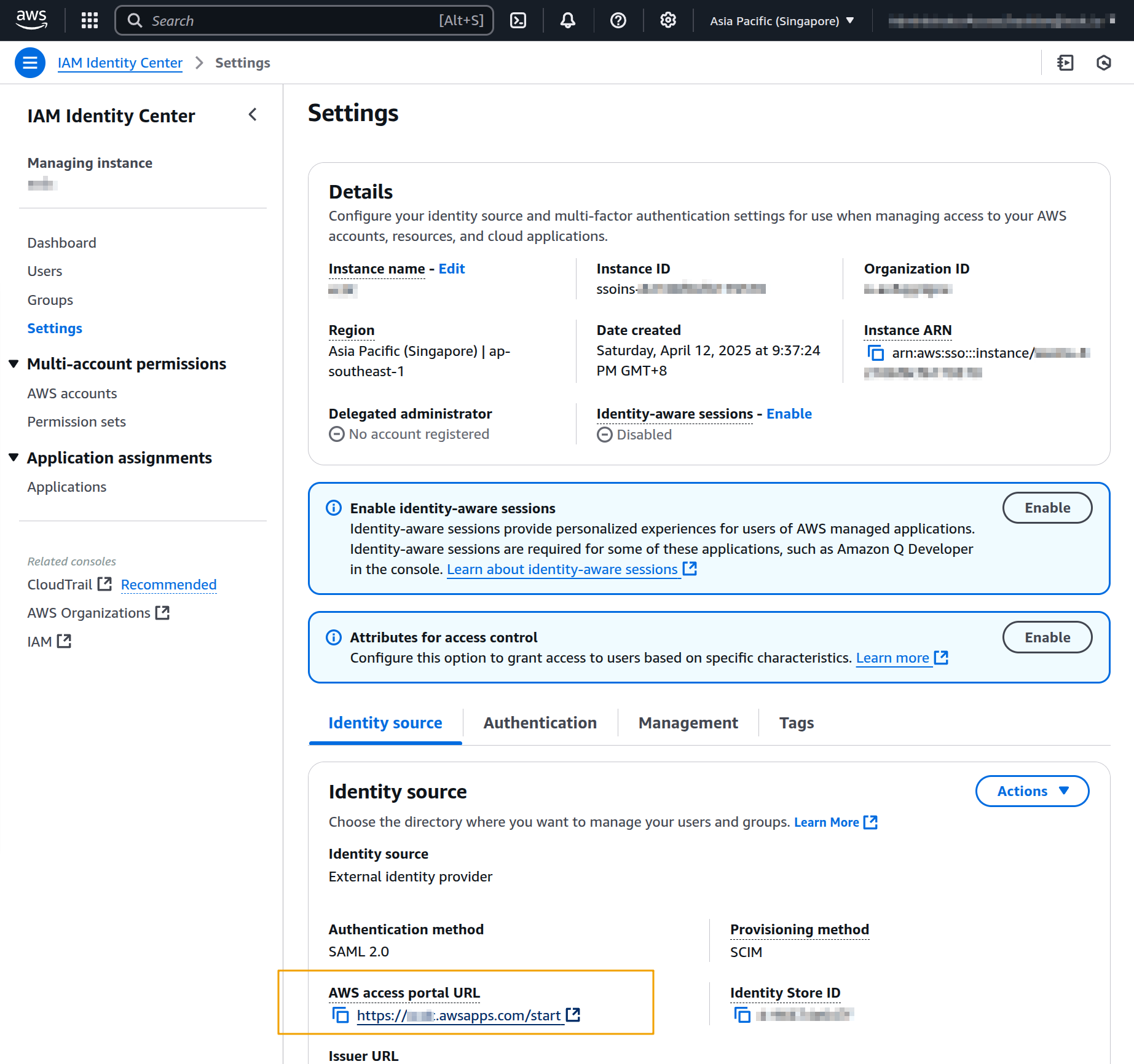
Open the link on a new browser tab, and it should redirect you to login to your Google Workspace account.After successful authentication, you will land on the AWS access portal, confirming that the SAML integration is working correctly.
wrap up
With single sign-on and user provisioning configured, you have successfully centralized your identity management. The next critical step is to manage permissions within AWS Identity Center by creating Permission Sets — collections of IAM policies—and assigning them to your synchronized Google Workspace users and groups. This ensures that your users have the appropriate, least-privilege access to the various AWS accounts managed by the Identity Center, completing the setup for a secure and streamlined multi-cloud environment.